Secure application development has become a significant aspect of software development. Every Python developer should know using the hashing and encryption libraries to better secure the data in transit & at rest associated with the application.
In this article, you will learn about how to implement hashing & what are its different advantages while implemented in the code.
What is Hashing?
Hashing is the method of transforming a piece of given information into another irreversible value. Programmers use the hash function to generate the new value (fixed length string) as per the mathematical algorithm defined within it.
The outcome of a hash function is known as a hash value or hash. Unlike encryption and decryption, where a given value if converted to encrypted value - we can reverse it back to its original value through decryption; hashing is one way and cannot be reverted back to its original value.
They are also known as cryptographic hash algorithm. MD5, PBKDF2, SHA-1, SHA-256, Crypt_MD5, NT Hash, PHPass, etc., are common examples of cryptographic hashing algorithms.
Why Python developers need to use Hash?
Whenever an authentication mechanism requires verifying a user along with some private credential like a password, the app must never store the password in plaintext. It is because, if an attacker finds the database or hacks it using SQL injection or some other database hacking technique, they will easily find the plaintext passwords.
They can use those compromised credentials to gain access to any account. Almost all companies like Facebook, Google, Amazon, etc., use the common method to store passwords – i.e., by hashing the passwords when a password is provided.
Also, many security experts recommend using a 'salt' when hashing and storing the password in hashed form.
Method 1: The hashlib Python Library:
The hashlib module acts as a common interface for Python developers from where they can leverage any well-known hash algorithm to securely store values and passwords.
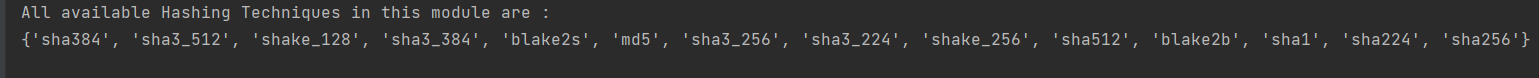
It includes hashing algorithms like 'sha384', 'sha3_512', 'shake_128', 'sha3_384', 'blake2s', 'md5', 'sha3_256', 'sha3_224', 'shake_256', 'sha512', 'blake2b', 'sha1', 'sha224', 'sha256', etc. The terms "secure hash" and "message digest" gets used interchangeably.
The older algorithms are called message digests while the newer hash algorithms are called secure hash. There are different functions of the hashlib module. 2 Popular of them are:
encode() : It helps in converting the string into bytes that will be acceptable by hash function.
hexdigest() : It helps in returning the encoded data in hexadecimal format.
Check all Algorithms with Hashlib:
import hashlib
# prints all available hash algorithms
print("All available Hashing Techniques in this module are : ")
print(hashlib.algorithms_guaranteed)
Output:
Generating different types of SHA hash values:
SHA is one of the most widely used hashing algorithm. Each of the SHA algorithm generates different values for the same string depending on the algorithm used. Here is a program generating different hash value.
import hashlib
str = "Gaurav Roy"
result = hashlib.sha384(str.encode())
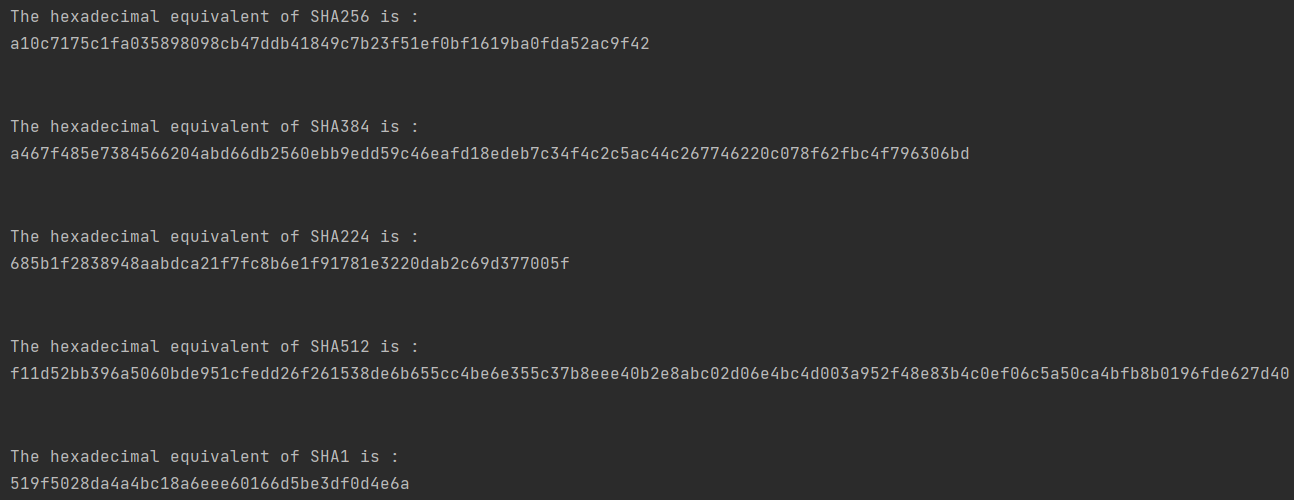
print("The hexadecimal equivalent of SHA384 is : ")
print(result.hexdigest())
print("\n")
result = hashlib.sha256(str.encode())
print("The hexadecimal equivalent of SHA256 is : ")
print(result.hexdigest())
print("\n")
result = hashlib.sha224(str.encode())
print("The hexadecimal equivalent of SHA224 is : ")
print(result.hexdigest())
print("\n")
result = hashlib.sha512(str.encode())
print("The hexadecimal equivalent of SHA512 is : ")
print(result.hexdigest())
print("\n")
result = hashlib.sha1(str.encode())
print("The hexadecimal equivalent of SHA1 is : ")
print(result.hexdigest())
Output:
Method 2: Using bcrypt Hashing Library:
Bcrypt is another password hashing library of Python created by by Niels Provos and David Mazières. It is based on the Blowfish cipher. This hashing library and function is the default password hashing algorithm for OpenBSD.
Other than Python, bcrypt is available for C, C++, PHP, Java, C#, JavaScript, etc. Encryption using bcrypt algorithm can generate hash & salt the password for Python programmers with the help of robust cryptography.
The computational cost of the algorithm depends on various parameters. So, it can increase with the processing power of computers. The computational cost in case of bcrypt is called the work factor or cost factor. Bcrypt-based hashing reduces cyber attacks on passwords, making brute force attempts and stealing passwords harder & slower.
The drawback of this algorithm is that to withstand any attack or to perform complex hashing, it gets slower and reduces user experience. To use it we have to first install the bcrypt in our system.
Basic Program to Hash a password using Bcrypt:
import bcrypt
passwd = b'Gaurav Roy'
salt = bcrypt.gensalt()
hashed = bcrypt.hashpw(passwd, salt)
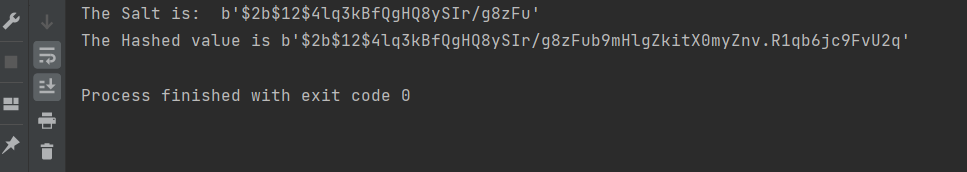
print("The Salt is: " , salt)
print("The Hashed value is", hashed)
Output:
Explanation:
Here, we will first import the bcrypt. Then we have created a variable passwd where we have stored the password string. Then we generated a salt using the bcrypt.getsalt() method. Now we use the bcrypt.hashpw() to hash the password along with the salt.
Here the password string and salt value goes as 2 parameters. Finally, we print the salt value and hashed value individually.
Program to check whether the Hashing of a password is correct or not:
import bcrypt
passwd = b'GauravRoy@123456'
salt = bcrypt.gensalt()
hashed = bcrypt.hashpw(passwd, salt)
if bcrypt.checkpw(passwd, hashed):
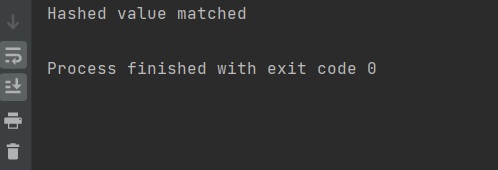
print("Hashed value matched")
else:
print("Hashed value does not matched")
Output:
Explanation:
Here, we will first import the bcrypt. Then we have created a variable passwd where we have stored the password string. Then we generated a salt using the bcrypt.getsalt() method.
Now we use the bcrypt.hashpw() to hash the password along with the salt. In this program we are checking using the bcrypt.checkpw() whether the password and its hash are same or not using the if statement. If it matches, the print function will generate a string "Hashed value matched"; otherwise, it will generate "Hashed value does not matched."
Conclusion:
We hope this article has given you two different approaches of how to hash passwords through Python scripts. The hashlib is advantageous than bcrypt because it has wide variations of hashing options and is faster than bcrypt.
Python programmers can use hashlib in web applications and data science operations without hampering the user experience. Bcrypt is beneficial to those who have already used it in BSD systems or in other programming languages.