IP addresses are one of the most significant elements of the internet, set to every device linked to a computer network or the internet. It contains information associated with our location and makes devices capable of two-way communication. A few ages back, people were unspecified that any hacker could track and steal our pieces of information and privacy through what we do over the internet. It is all possible only through our IP address.
Our IP address is like an identification number linked to our device that informs websites where our internet traffic is coming from, what we are interested in and our other search records. So, to maintain our privacy, we need to take some measures to prevent our information from revealing to others. This article will let us know how internet users mask their IP address for better prevention.
What is IP Address?
The internet requires a method to differentiate between specific routers, networks, and websites. Hence, our unique IP address provides the means of doing so. As we have already discussed, IP addresses are number series that tell the internet about our existence online. It includes an essential part of the working of the overall internet.
IP addresses specify and differentiate the billions of online devices. It includes laptops, computers, and mobile phones. It also helps these devices to communicate with each other.
There are two types of address sizes of IP addresses. These are IPv4 and IPv6.
- Ipv4 is version 4 of IP and is a 32-bit address. For example, 50.67.74.88
- On the other hand, IPv6 can generate four billion addresses and is the next generation of IP addresses. It is a 128-bit hexadecimal address.
Why do we need to mask our IP address?
There are several reasons for IP masking. These are as follows:
- Some countries monitor and keep an eye on their citizen's Internet activity. They might use this data against any citizen as an attempt to verify anti-government opinions that can lead to criminal charges or more alarming situations. A technique around this approach to make our IP not monitored is to mask IP address whenever we go online.
- One of the most significant reasons for hiding our IP address is to secure our data and privacy from the hands of hackers. Like the government, ISPs, and websites can track and seize information by using the IP addresses hackers can also use these to steal our privacies. It opens us up to malware attacks and other types of digital attacks.
- When we connect our devices to the internet, Internet Service Providers (ISPs) track our activities and rob information through the internet through our IP address. If we hide our IP address, this can prevent our data from getting tracked. When we connect to a VPN, the only thing our ISPs can see is that we connected our device to that network. VPN provides a means to stay private online and protects our privacy from our ISPs' prying eyes.
- Often, we find our school or workplace might restrict access to websites when we use their network and IP address. If we can hide our IP address, we can efficiently get freed from these limitations.
How to find my IP address on any device?
There are a few steps/ways to know our IP address in any operating system. The steps are as follows:
Find IP address on Windows:
Go to the “Windows Start” logo and right-click it, located in the left corner of our screen.
Click on "settings."
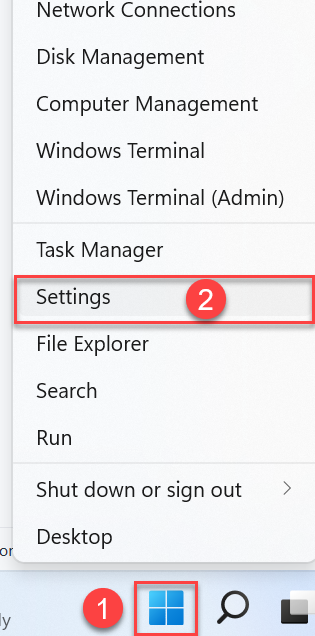
Select "Network and Internet."
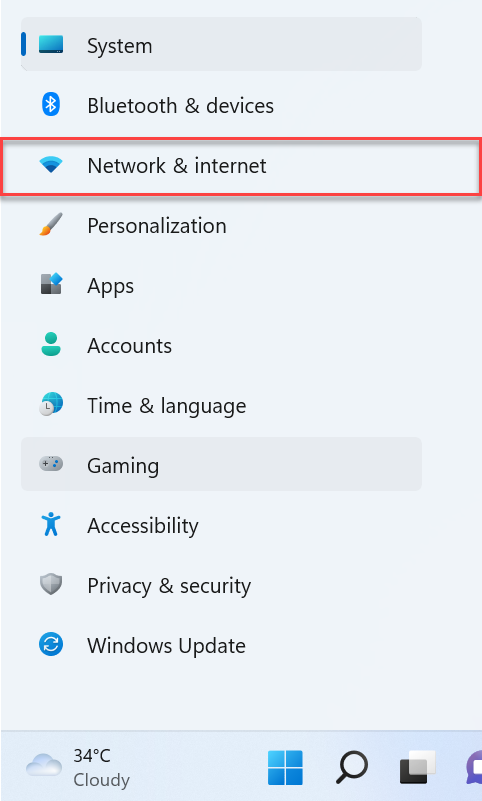
Click on the "Ethernet" or "Wi-Fi" option (based on our connection)
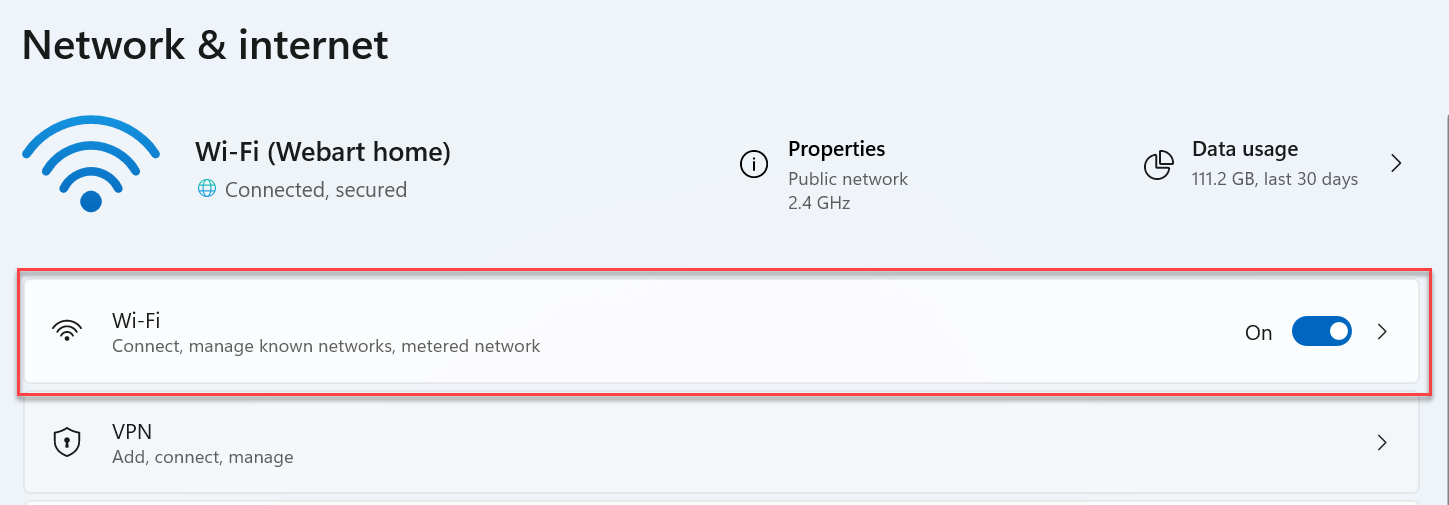
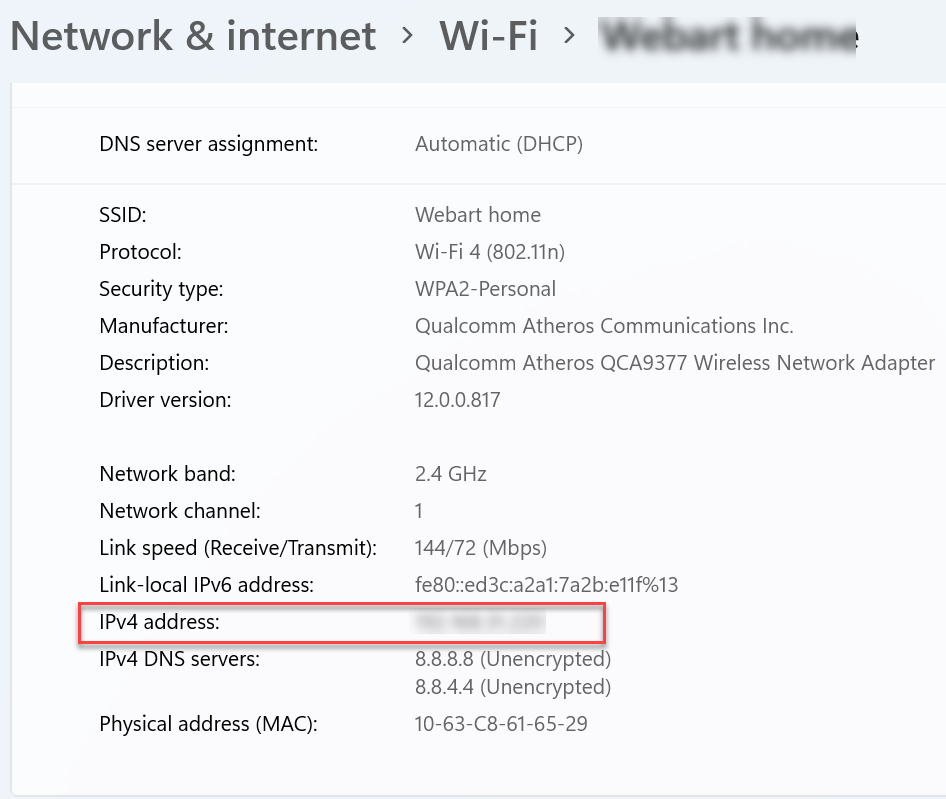
Select the "Network" icon, and our local IP address appears in the window under "IPv4 address."
Find IP address using Command Prompt:
- Go to the “Windows Start menu”.
- Type "Command Prompt" into the search bar (do not need to use the quotes).
- Alternatively, select "Run" if users do not have the search bar.
When the command prompt box appears, type and enter "ipconfig" ((do not need to use the quotes).
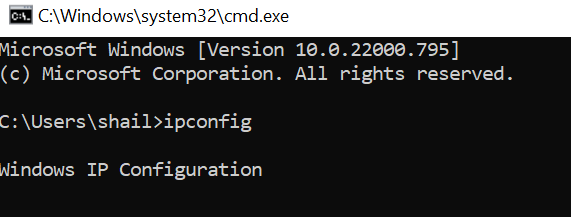
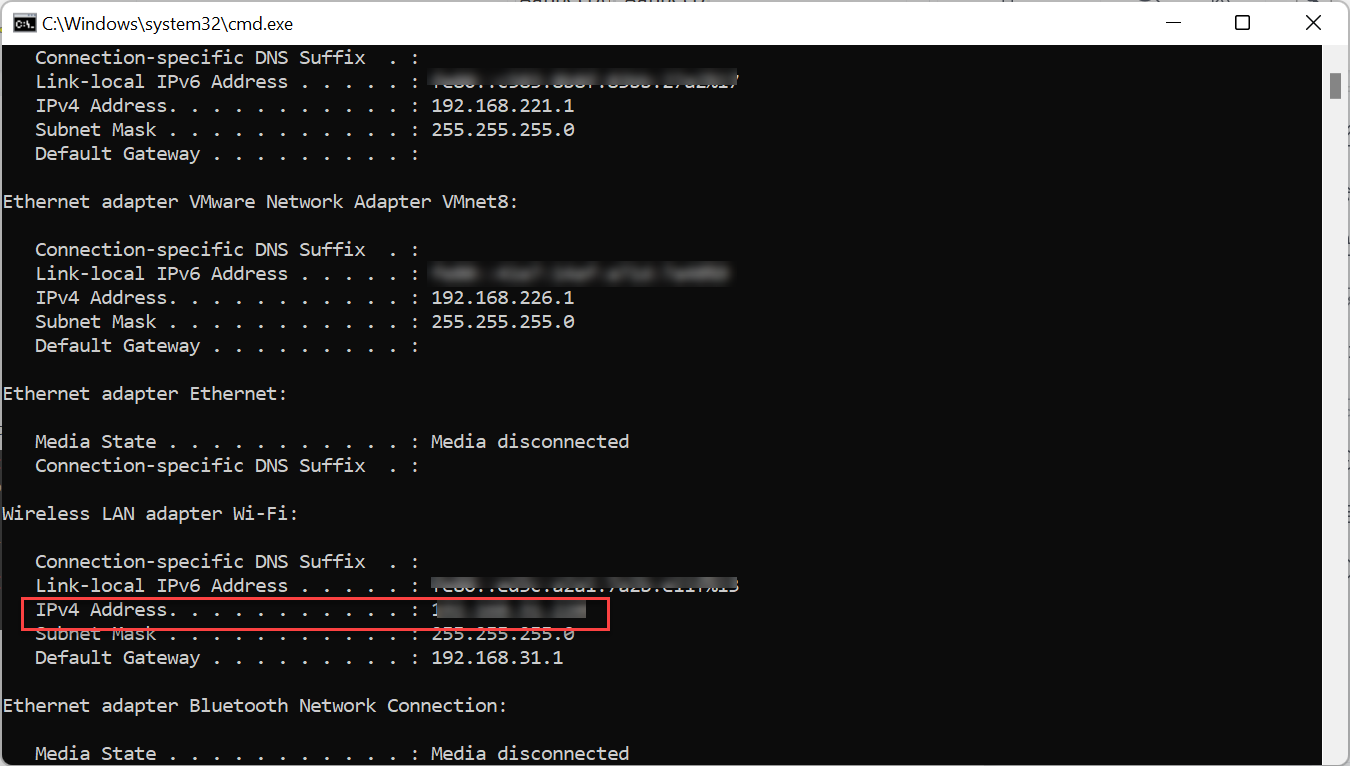
After giving the command, a window opens containing different network arcana sections with our local IP address.
Lastly, entering the "ipconfig" command in the Windows Command Prompt screen mentions our IP address with different other home network parameters or Wi-Fi networks.
Find IP address on macOS:
- First, go to the “Apple menu” and click it.
- Select “System Preferences”.
- Select the “View menu” and choose the “Network” or select “Network in the System Preferences window”.
- Select the network connection from the menu residing on the left.
- It will show our local IP address for a USB or Ethernet connection.
- We will see our IP address displayed under the connection status for the Wi-Fi connection.
Find IP address on Android:
First, go to “Settings” and select “About phone”.
Select “Status information”.
We can bypass this step on some Android versions and scroll to find the IP.
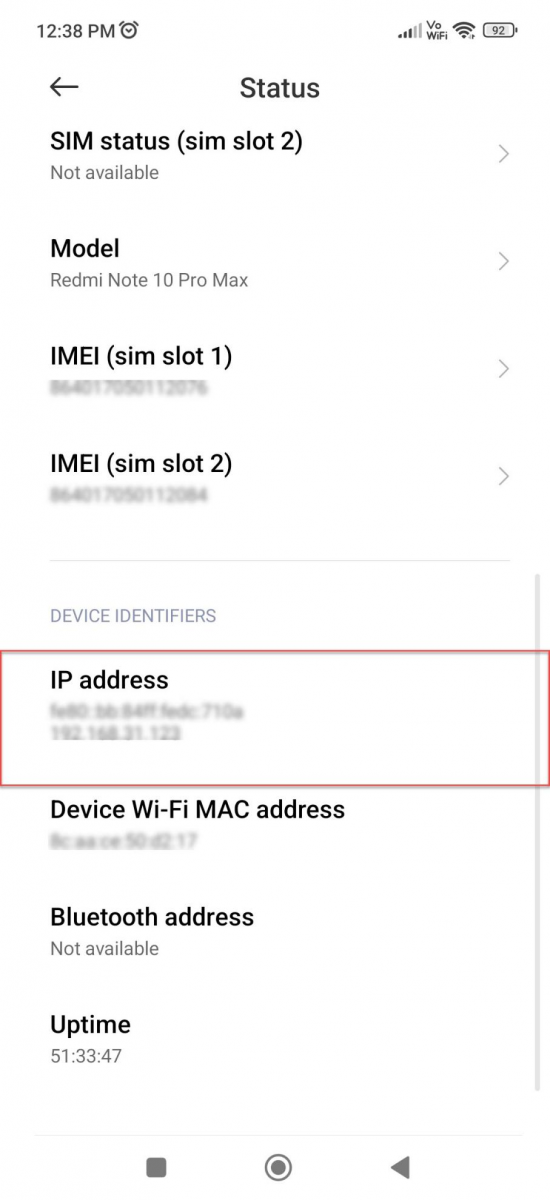
Scroll up and down to find the local IP address. It will show both the IPv4 and IPv6 IP addresses.
Eight ways to hide our IP Address:
The list of the 8 different ways we can use to musk our IP address is as follows:
Use of VPN to mask our IP address:
VPN or Virtual Private Network is a private network service that hides private intranets, encrypts all data sent and received from the internet, and routes it via a VPN server in a distinct location. The VPN server functions as an intermediary between our device and the internet.
So online sites and apps only track the server's IP address but not our own.
A VPN encrypts all our traffic in both the browser and other applications and then passes traffic advancing to its destination. Some VPNs that we can use risk-free are as follows:
- NordVPN
- Express VPN
- Cyber Ghost
- Private Internet Access
- Private VPN
- IPVanish VPN
Steps to mask the IP address:
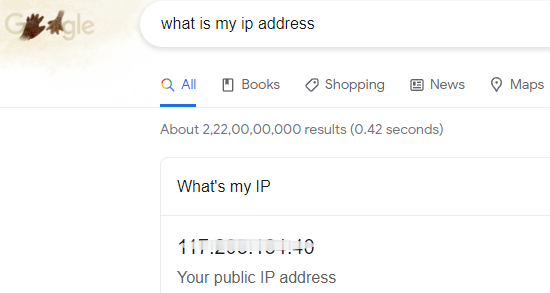
First of all, we need to know our current IP address. Use Google and type "what is my IP address?" to get the IP.
Once we note down our IP address, we have to sign up for a VPN. One of the most popular VPNs is NordVPN.
Then we download the VPN app on our device. Windows and Mac users usually get these apps from the provider's website (online). iOS and Android users need to download the VPN applications from the Google Play and App Store, respectively.
After we install the VPN app, we can run it.
We need to sign in using the account credentials we created in step two.
Then, we have to select a server location or server. Our generated unique IP address will be that of this server.
Then, clicking on the Connect button or double-tapping the server can create a connection. We can now connect our devices to the internet through a private network.
Once we establish the connection, we will get a new unique IP address. To assure the IP, we can use Google and type "what is my IP?” Our new IP address should be distinct from the previous IP.
VPN having these features can help us to mask our IP more securely and efficiently:
Leak protection:
VPNs are to protect all the internet data that our devices are sending and receiving, but unfortunately, they leak sometimes. When our information is exposed, there is a more chance of hacking. So, we should look for those VPNs that include IPv6, DNS, and WebRTC leak protection.
Private DNS servers:
DNS stands for Domain Name System. It functions as a directory for the internet by decrypting domain names like "techno.com" into IP addresses that our device can use to communicate.
DNS servers can see our IP address when we send a request to any website for something, even when connected to a VPN, as we likely use DNS servers used by our Google or Internet Service Provider (ISP) by default.
For this reason, it is necessary to use a VPN that uses its DNS servers so that we never get exposed to a third party with our IP address.
No-logs policy:
Our VPN provider should not keep or register records of our internet activities or any contact details that anyone could use to identify us.
Kill switch:
A network lock or kill switch can quit our device from the internet connection if our VPN connection drops on any basis.
Download Steps for VPN:
This article has provided the best VPN list. It is up to our choice with which VPN will be great to start.
Then, go to the preferred website of that VPN provider (always be aware that we should not accidentally download the cracked VPN, that can be very dangerous as it is fake and unlawful).
We need to create an account, download the app and log in.
After downloading the VPN, we only need to access the app to the server to be able to surf anonymously, privately online.
Use of proxy server to hide our IP address:
The proxy server acts similar to the VPNs. The proxy server manages our internet traffic and records on our behalf. In other words, a proxy server acts as an intermediary between our device and the internet.
DNS servers and Websites track the IP address of the proxy server and not our main IP address. It sits in front of a client or network of clients, delivering requests received from end-users.
At the same time, it also receives and returns responses from servers. Hide.me is one of the best proxy servers available for free.
Advantages of VPNs over Proxy Servers in IP masking:
We can say that VPN is a type of proxy. But precisely, the proxy servers refer to SSL, SSH, and SOCKS proxy. Generally, these proxy servers are less reliable than VPNs.
Compared to other security services offered by VPNs, they are less preferred, but they do mask our IP address from DNS servers and websites. Unlike a VPN, most proxies would not encrypt our online data, and they also would not hide our IP address from a third party who can intercept our privacy on the way from our device to the proxy server.
Proxies are also more vulnerable to man-in-the-middle attacks as this lack the authentication of VPNs. An attacker can personate himself as a proxy server to rob our privacy. Thus, we prefer proxies for a temporary, immediate solution and are not for a long-term privacy plan.
Download Steps for Proxy Servers:
We can download proxy servers to mask our IP address based on our operating system. The following steps with the respective operating system will guide us through the download process:
For Mac:
- Go to the Safari app and click on "Preferences."
- Then select the “Advanced” option.
- Next, go to “Change Settings”.
- We need to update our settings. And then, we will get a new, protected window.
For Windows:
- Go to administrative templates and click Windows Components.
- Then select “Data Collection and Preview Builds”.
- We need to configure Authenticated Proxy Usage.
- Windows users have to set it to “Enable”.
- Lastly, click on Apply.
For iOS:
- Go to Settings and click Wi-Fi.
- Choose “Network info” and click on the “HTTP proxy section”.
- iOS users have to choose the Manual option and choose on Edit Proxy Settings.
- Then turn on "Authentication."
- Lastly, they have to save it by going back to the Wi-Fi Selection page.
For Android:
- Go to Settings and click “Wi-Fi”.
- Clock Network Name.
- Select “Modify Network”.
- Select “Advanced” and click on “Manual”.
- Then we need to enter our Hostname and Proxy Port.
- Lastly, all android users should not forget to click Save.
Use of Tor server to hide our IP address:
Tor or The Onion Router is an open-source, free, encrypted network managed by thousands of volunteers. Tor operates an onion-style routing method for transferring data.
When we use the Tor browser to communicate or access a website through the internet, the Tor network does not directly connect our device to that website. Instead, the network intercepts the traffic from our browser and jumps to a random number of other Tor users' devices before handing the request to the final website destination.
As soon as we quit the website, our cookies will get cleared, and our browsing history too. The website would not see our main IP address. But instead, it will track on the one the Tor has replaced.
Tor is an excellent tool if we want to keep our IP address secret. However, the service is inadequate for torrenting or streaming as it often locates the nodes in the incorrect regions.
But most importantly, Tor is in the eye of the FBI (Federal Bureau of Investigation) and other surveillance agencies, which might indicate that if our browsing activities are marginally illegal, we might not be hundred percent unidentified on the Tor browser.
Download Steps for Tor:
First, go to the website of the Tor Project.
From there, install the browser.
Use of Browser Extension:
While we get the above means to mask our IP address, we can also use our respective browsers to hide our IP. Our browsers provide plug-ins, extensions, or add-ons that can help us secretly browse the internet without exposing our main IP address, for example, Google Chrome, Mozilla Firefox, etc.
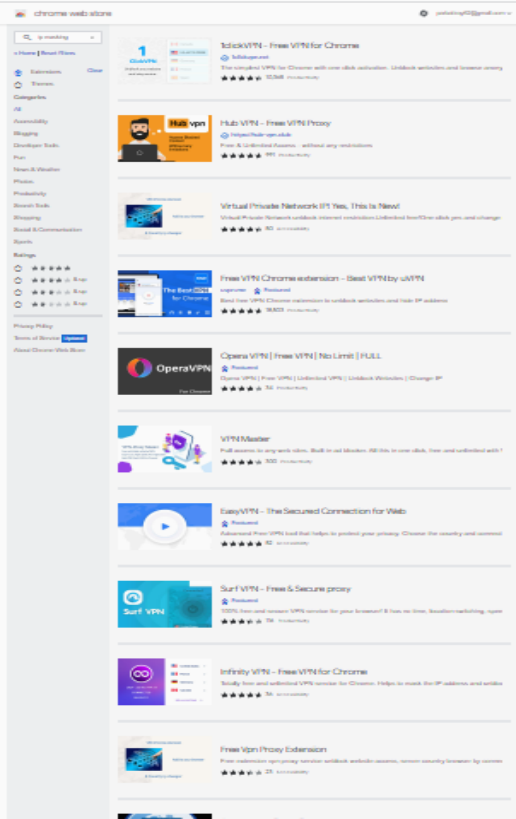
Let us take our Google Chrome as an example. Google and type "Chrome extension Store." It will direct us to the Chrome Web Store. Click on the link and in the search option ("Search the store"), type IP masking. It will provide the list of all the Chrome extensions for IP masking.
Here is a list of all the add-ons or extensions available in Google Chrome:
- Hub VPN
- VPN Free
- Hide My IP VPN
- ZenMate Free VPN
- Hotspot Shield Free VPN Proxy
- VPN Unlimited
- Browsec VPN

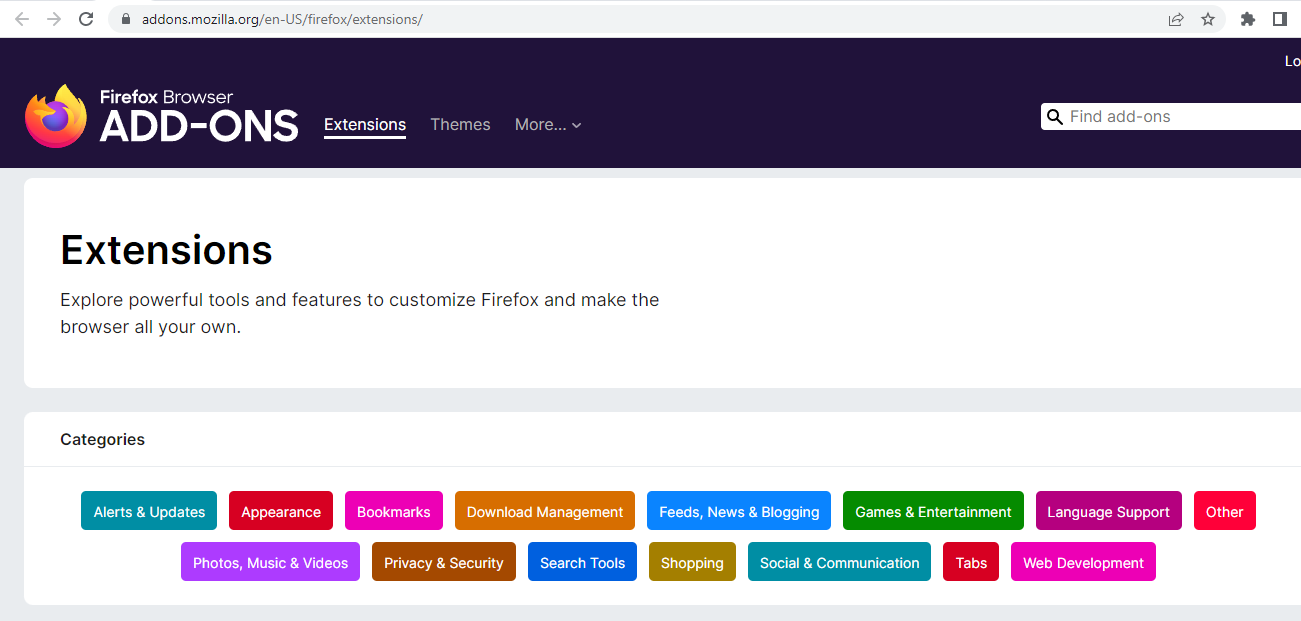
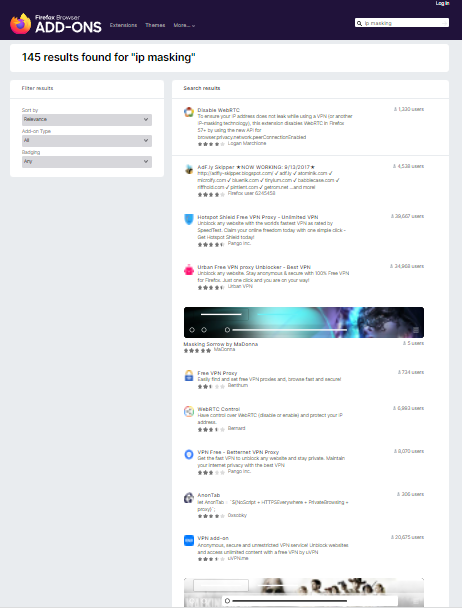
The list of Extensions available in Mozilla Firefox is as follows:
- Disable WebRTC
- Hotspot Shield Free VPN Proxy
- Urban Free VPN Proxy Unblocker
- VPN Free
- VPN Add-on
- Windscribe
- Touch VPN
Connect to different networks:
When we change the networks, our IP address also gets changed. We can use distinct networks, like public or private Wi-Fi, to get a unique IP address. It is advantageous when we think that the IP address we have been using has been barricaded, tracked, or compromised. Also, if possible, we can choose those networks that require passwords.
Public or private Wi-Fi hotspots and various open networks can also be the tracking grounds for cybercriminals that can take advantage of the absence of authentication and encryption.
This is one the most significant disadvantage of these networks. Even the websites might also get information about the location from where we are connecting, and we would not be able to browse websites that are not available in our region.
Unplugging our Modem:
The Internet Service Provider has assigned us our unique IP address. Most ISPs provide a dynamic IP address, which indicates that if we unplug our modem and re-plug it, there are chances that we will get a different IP address.
We may have to wait for a short time for the DHCP lease (our IP address assignment) to expire, though. The longer we leave the modem unplugged, the chances of the tactic to work more likely. Also, it is better to leave it unplugged overnight if we have to. But the process is not guaranteed to work. But this process is not preferred for security purposes.
Through ISP, we can change our IP address:
The ISP is an organization that provides the facility, service, accessing or using the internet to users. They provide us with a unique IP address.
So if we want to change our IP address for any reason, we can try by contacting the Internet Service Provider by giving them a call. We need to know our current IP address and our account information on hand.
But we cannot expect that this new IP address will remain the same forever. Because Internet Service Providers frequently recycle the IP addresses to maintain the fixed number of available IP addresses.
Our IP address will likely change once a time, and the process of a temporary IP address that the ISP provides is known as dynamic IP addresses. We can also request the ISP for a static IP address that will never change.
But this will add to an extra cost and other application processes.
Renewing IP address to change the Private IP address:
We can renew our IP address by entering a few simple commands into our Windows Command Prompt or Mac Terminal. The following steps will let us know how to renew our IP address:
Steps for Windows:
First, we need to go to "Search" and type Command Prompt.
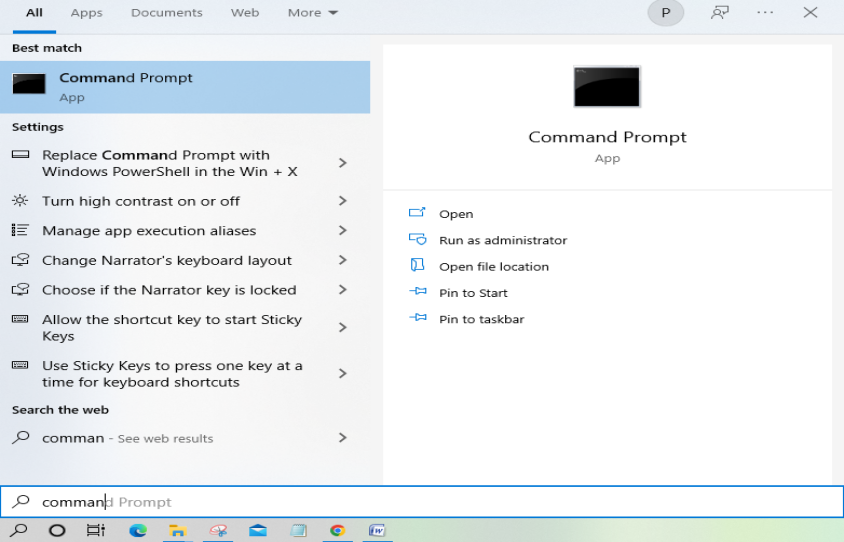
- Windows users have to right-click on it and select “Run as administrator”.
- Type and enter “ipconfig /release”, and lastly, enter “ipconfig /renew”.
Steps for MacOS:
- First, go to the “Apple” menu and click it.
- Open “System Preferences” and select “Network”.
- Mac users need to highlight the network to which they connected in the left pane
- Click “Advanced” and click on the “TCP/IP” tab
- Lastly, select “Renew DHCP Lease”
How to know other’s IP address using code?
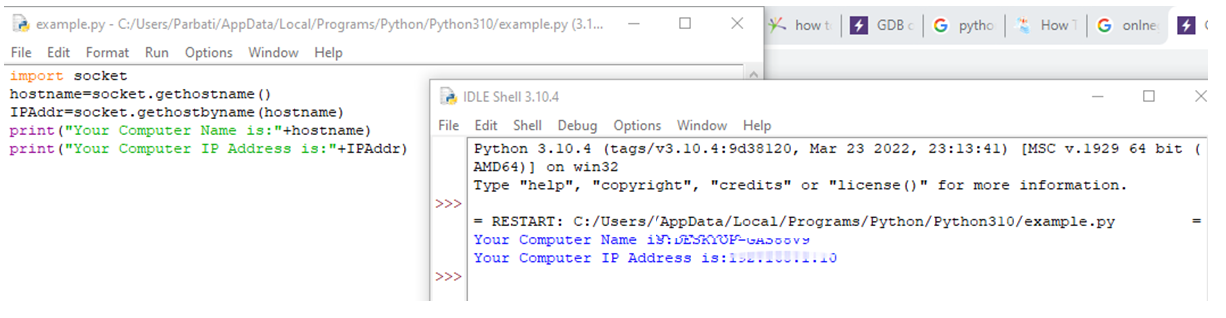
Use this Python code to get to know the IP address of other users.
Code Snippet:
import socket
hostname = socket.gethostname()
IPAddr = socket.gethostbyname(hostname)
print("Your Computer Name is:" + hostname)
print("Your Computer IP Address is:" + IPAddr)
Output:
Conclusion:
We hope this article has catered to the steps and ways about how to mask our IP address and how we can find our local IP address supporting any Operating system. IP masking is one of the best techniques to secure our privacy and information. Users can go through any of the steps mentioned above if they prefer to be more practical.