How To Maintain the HCI Keystore?
For HTTPS-based communication in the cloud integration tenant, the root certificate of the receiver system provided in the previous step is needed in the cloud integration tenant’s keystore.
Moreover, in order to use client certificate authentication, a signed key pair including complete certificate chain is needed in the cloud integration tenant’s keystore.
Please follow the steps below in order to manage HCI Keystore:
The first version of Keystore Monitor cannot import single certificates or keys, therefore, the root certificate of the backend and the signed private key including certificate chain need to be maintained in the external keystore maintenance tool such as the Keystore Explorer.
All new provisioned cloud integration tenants have inbuild private key pair pre-delivered by SAP, which you can be used by you for your communications. But, if needed you can also create your own private key pairs for the cloud integration tenant.
In order to add the root certificate of the receiver systems private key, please open any existing keystore in Keystore Explorer or to create a new keystore. It will be easy for you to just create a new keystore please select JCEKS as a type for the new keystore.
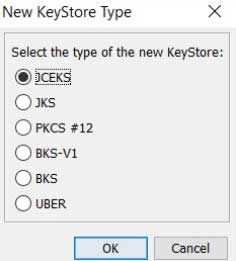
Now under tools select Import Trusted Certificate and then add the root certificate of the receiver backend. Then give it an alias in the customer namespace, please keep in mind that you are not allowed to use aliases with prefix sap_, hcicertificate and hcimsgcertificate.
You can add additional certificates if needed and ave the keystore with a password as .jks file.
Note: The password as this will be needed during import in Keystore Monitor.
Import Keystore in Keystore Monitor
In order to import the created keystore file please open the Keystore Monitor available in the Operations View in Web in section Manage Security. All certificates and private key pairs contained in the tenant keystore are listed, the pre-delivered key pairs by SAP cannot be changed.
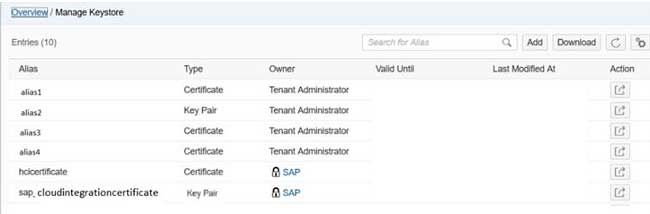
Now upload the keystore with the help of Add button on the top of the monitor. Then browse the *.jks file and enter the password you gave in the previous step. The root certificates available in the keystore file will be added to the existing entries for owner Tenant Administrator with the aliases used in Keystore Explorer.
Authorization
In order to maintain keys and certificates in Keystore Monitor, your user needs the Group Role AuthGroup.Admin or Single Roles IntegrationOperationServer.read, NodeManager.read and NodeManager.deploysecuritycontent.